ISACA. (2018). COBIT 2019 Design Guide: Designing an Information and Technology Governance Solution. Retrieved from www.isaca.org
ISACA. (2018). COBIT 2019 Framework: Governance and Management Objectives. Retrieved from www.isaca.org
ISACA. (2018). COBIT 2019 Framework: Introduction and Methodology. Retrieved from www.isaca.org
ISACA. (2018). COBIT 2019 Implementation Guide: Implementing and Optimizing an Information and Technology Governance Solution. Retrieved
from www.isaca.org
National Institute of Standards and Technology - NIST. (2017). NIST Special Publication 800-53 Revision 5. U.S. Department of Commerce. Retrieved
from https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/draft
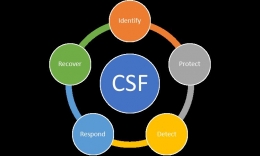
National Institute of Standards and Technology - NIST. (2018). Framework for Improving Critical Infrastructure Cybersecurity Version 1.1. U.S. Department of Commerce. doi:10.6028/NIST.CSWP.04162018
North American Electric Reliability Corporation. (2020). NERC CIP Reliability Standards. Retrieved from https://www.nerc.com/pa/Stand/Pages/
CIPStandards.aspx
Office of Government Commerce. (2007). ITIL Continual Service Improvement. The Stationary Office. Office of Government Commerce. (2007). ITIL Service Design. The Stationary
Office.
Sabillon, R., Serra-Ruiz, J., Cavaller, V., & Cano, J. (2017). A Comprehensive Cybersecurity Audit Model to Improve Cybersecurity Assurance: The
CyberSecurity Audit Model (CSAM). Proceedings of Second International Conference on Information Systems and Computer Science (INCISCOS).10.1109/INCISCOS.2017.20
The Institute of Internal Auditors - IIA (2016). Assessing Cybersecurity Risk: Roles of the Three Lines of Defense. Supplemental Guidance - Global Technology Audit Guide (GTAG). IIA.